Security testing is a Non–Functional testing process performed to check whether the application secures data from vulnerable attack or unauthorized access. Software security is about making software behave in the presence of a malicious attack.
Contents
Need To Conduct Security Testing
- The primary purpose of security testing is to identify the vulnerabilities and subsequently fixing them.
- It helps in improving the current system and also helps in ensuring that the system’s stability.
- Security testing helps in finding out loopholes that can cause loss of confidential data.

Basic Principles of Security Testing
Security Testing aims at verifying 6 basic principles as listed below:
- Confidentiality
- Integrity
- Authentication
- Authorization
- Availability
- Non-repudiation
Security Testing Techniques
- Injection
- Broken Authentication and Session Management
- Cross-Site Scripting (XSS)
- Insecure Direct Object References
- Security Misconfiguration
- Sensitive Data Exposure
- Missing Function Level Access Control
- Cross-Site Request Forgery (CSRF)
- Using Components with Known Vulnerabilities
- Invalidated Redirects and Forwards
OWASP Zed Attack proxy (OWASP ZAP)
OWASP is an open-source web application security scanner developed at the Open Web Application Security Project (OWASP).
OWASP ZAP helps us automatically find security vulnerabilities in a web application. It is a great tool for penetration testers as well as functional testers. OWASP alerts about security vulnerabilities of an e-commerce website.
Features of OWASP
- Intercepting Proxy
- Automated Scanner
- Passive Scanner
- Brute Force Scanner
- Fuzzer
- Port Scanner
- Spider
- Websockets
- REST API
How To Find Security Vulnerabilities Using OWASP?
Step 1:
Install Zed proxy.
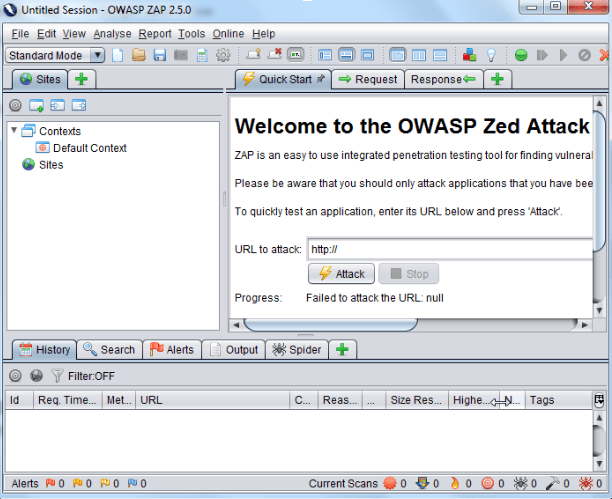
Step 2: Enter the URL in the tab and start the attack zap. It will automatically record all URL’s from your selected domain by crawling through your web application.
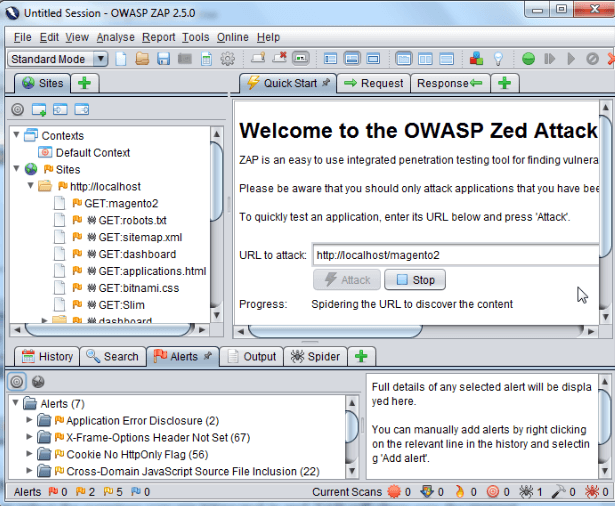
Step 3: ZAP displays several possible vulnerabilities in the warning alert section. We can select the warnings we are interested in and ZAP will show you the request and response raw data as well as hints on how to fix the vulnerability.
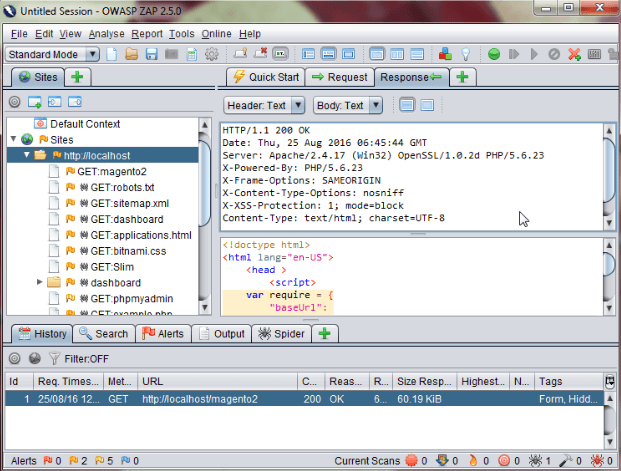
Step 4: Quick start is just a basic security check for your application. In order to be more thorough testing, you need to configure ZAP as a proxy. This allows ZAP to record the traffic and use that traffic for a replay attack while modifying the request parameters.
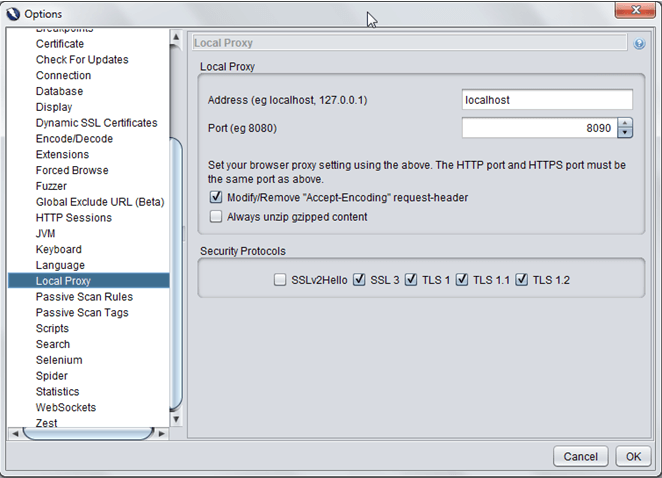
 Step 5: Open ZAP > Tools > Options > Local Proxy. Configure the address and port on which ZAP will listen for requests.
Step 5: Open ZAP > Tools > Options > Local Proxy. Configure the address and port on which ZAP will listen for requests.
- Address: local host
- Port: 8090
Step 6: Change local browser to use this proxy. In most browsers, you can do this under Settings > Network > Proxy Settings. Now you can use your browser to access your web application. ZAP will automatically record the traffic.
Step 7: Right click on a recorded site and configure ZAP to scan the found URLs.